| Creating new files in Photoshop is easy: click File and then New.

Set the height, width, and resolution of the new file in the dialogue box.

Opening files in Photoshop is just as easy: the command File>Open can be used to open most graphics files.
Once you’ve created or opened a file and edited it, you can save your file in a number of different formats. To save the file in its current format, use File>Save. If you want to save it as a different type, you can use File>Save As. We’ll discuss saving later in the tutorial; for now it’s OK to save your images in their original format.
The Flash Toolbar
Let’s start learning about flash toolbox, it has many tools to draw graphic, fill color, gradient color and modify the shape of the drawn by the tools. Some tools have hidden tool that is indicated by a little black triangle shape that is situated right bottom corner of the tools. I have given below every tool’s description so read carefuly.

In the tool section in the toolbar, we have different type of tool to make graphic and modification in that. All the tools are fully describe below.
Selection Tool: Selection tool helps to select and modify the object shape. We can move any object which we have imported and drawn. We can delete the any part of any formatted picture but remember the picture should be break (To make break picture, press Ctrl + B key).
Subselection tool: When we need modification to make different shape of the drown graphic in the document, we need a tool that is Subselection tool. It highlight the anchor point of the graphic by click on that to arrange point and get different shape as required.

Free Transform tool: Free Transform tool is very important tool, this tool helps us to scale, reflect of the picture and we can rotate the object from the particuler point. we can also skew of object as per our requirement.
Gradient Transform Tool : With the help of this tool you can scale and rotate of the Gradient. When you fill the Gradient on object. Select the Gradient Transform tool or pres F. As you click on Gradient Transform tool a bounding box will appear on the objects. then you can work this bounding box Ex. Moving the gradient, move the focal point. (focal point applicable only Radial gradient.), increase and decrease of gradient, rotate the gradient as required.
Lasso Tool : Lasso tool is a free hand selection tool. you can use this tool to select the object as you required and delete. when you select lasso option one magic wand tool and magic wand setting also appear down of the tool pallet, you can change the setting of this tool.
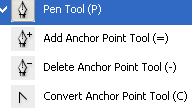
Pen Tool: Pen tool used to draw graphics by the anchor points and create line path in the document.
Add Anchor Point: We can add the more anchor point on the path and any graphic drawn by any tool by clicking on the path.
Delete Anchor Point: We can delete the anchor point on the same way by Clicking on the Anchor Points
Convert Anchor Point: We can modify the path with the help of this tool.
Text Tool: Select the text tool to type text on the document, click on the document with selected text tool a text area will appeared on the document, write the text on the box. You can scale the text area by scaling and more options will appear on the properties panel.
Line Tool: With the help of line tool we can also make the curve path and draw straight line. To make curve graphic we should draw a straight line then make curve by the help of Subselection tool.

Rectangle Tool: This section has different type of shape tool to draw shape on the document like Rectangle, Oval, Rectangle Primitive, Oval primitive and polyStar shapes. You can also modify the tool property to get different type of shapes.
Pencil Tool: This is a freehand tool that’s used to drawing. when you click on the pencil tool more option will appear bottom of the tool pallet. you can create those shapes also.
Brush Tool: It’s also a freehand tool and used to crate drawing and lines in the document. The different mode of the tool are also available in the flash to get different brush effect, select brush tool some more option will appear on the bottom of the toolbar make setting and apply on.

Ink Bottle: This tool is used to change the color of stroke color and other options.
Paint Bucket: The paint bucket helps us to fill selected color in the selected area and graphic, choose any color from the color pallate and fill by the paint bucket tool.
Eye Dropper Tool: Eye Dropper tool helps to pick any color from the picture and graphic, As you want to fill a color that is not in the color pallate, open colored picture and pick color by eye dropper tool and fill anywhere in the document as required.
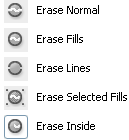
Eraser Tool: This is a eraser tool we can erase the object and unwanted area in the document by five different way, the list is given below.
The view section in the toolbox, we have two tool those are used to move the document and zoom picture, the tools are described below.
Hand Tool: With the help of hand tool, in the zoom mode of the document it is used to move document on any side or just hold down the space bar and move file with the help of the mouse.
Zoom tool: With the help of zoom tool, we can see the the object and picture in the zoom mode and modify on the right place as required and come back to actual size press double click on the zoom tool.
The color section in the toolbox, we have two tool those are used to fill stroke and foreground. The tools are described below.
Stroke color: When we draw any graphic by the help of any tool, the stroke automatically appear with the graphic with same graphic color. If we want to draw graphic with different stroke color, select stroke color before drawing.
Fill Color: First choose foreground color as you want to fill in the graphic then draw graphic on the document, it can also change after the drawing but the tool is given in the toolbar so make first color setting.
The animation in Flash
|











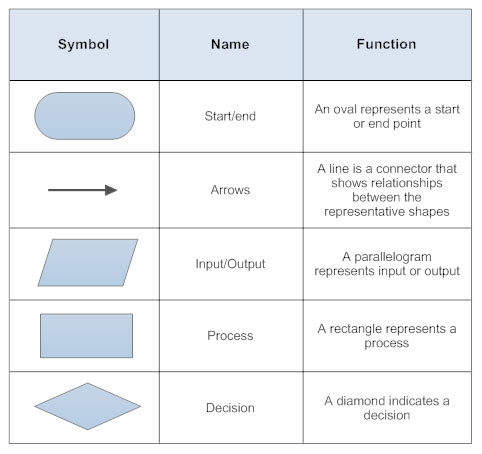
![[Flowchart Symbols]](https://i0.wp.com/www.wiley.com/college/busin/icmis/oakman/outline/chap05/images/f5_02.gif)


































